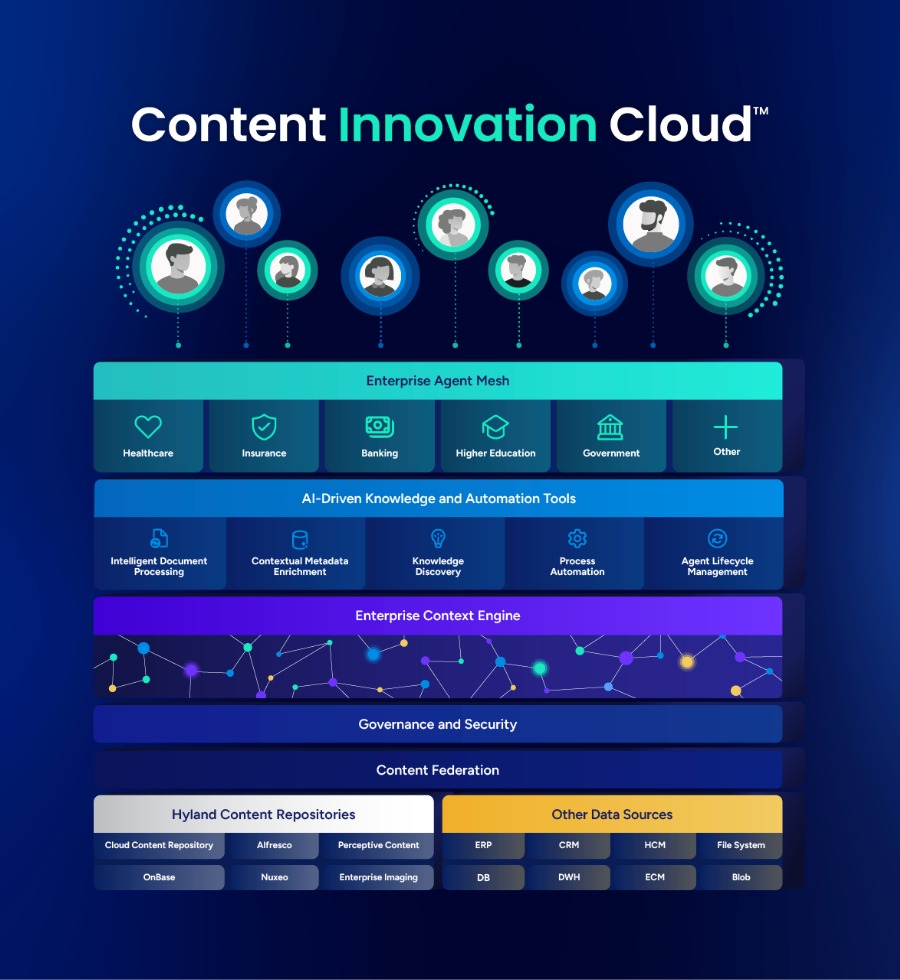
BMC AMI Security recognizes that ransomware represents one of the most disruptive threats to enterprise mainframe environments. This includes threats that target not only data but also operational continuity and business trust. As mainframes continue to anchor global financial transactions, supply chains, and government operations, the impact of a ransomware attack extends far beyond IT, it reaches the very core of business resilience. BMC has made it a mission to ensure that prevention and response are not reactive measures, but foundational capabilities built into the heart of mainframe security.
At the center of this mission, BMC AMI Security integrates the principles of the NIST Cybersecurity Framework (CSF) which is Identify, Protect, Detect, Respond, and Recover into every layer of mainframe defense.
- Through continuous asset discovery and behavioral baselining, AMI Security identifies vulnerabilities and risks before they can be exploited.
- Using intelligent access controls and encryption, it protects sensitive system datasets and credentials from unauthorized access or privilege escalation.
- Advanced AI-driven anomaly detection and behavior analytics provide early-warning detection of ransomware indicators, enabling proactive intervention.
- During an active incident, AMI Security automates response actions while halting compromised sessions, terminating batches, and alerting stakeholders to malicious actions. Additionally, AMI will determine what user ID’s were used in an attack, datasets touched and time of attack to determine which immutable backup is safe for recovery. Finally, AMI Security will determine if any backdoors or president threats remain to prevent a repeat attack upon recovery.
- Following an attack, its forensic visibility and detailed session playback allow organizations to recover rapidly, validate the integrity of restored systems, and close gaps to prevent recurrence.
Aligned to the NIST framework, these integrated capabilities provide a structured, continuous loop of protection ensuring organizations maintain operational resilience in the face of evolving ransomware threats. It transforms mainframe security from static protection into an adaptive, intelligent system capable of detecting threats early, containing them instantly, and restoring operations swiftly. This proactive, policy-driven resilience ensures that even in the face of advanced ransomware campaigns, enterprises can continue to operate with confidence by protecting their most critical assets and preserving business continuity.
BMC Mainframe Security offers some unique approaches to harden security and assist in recovery. Modern cyberattacks are no longer simple, one-time breaches, they are persistent, stealthy, and adaptive, often leveraging legitimate user credentials to avoid detection. For organizations relying on mainframe systems to run core business operations, even a brief compromise can have devastating operational and financial consequences.
BMC AMI Security combats this by combining Behavior Analytics and Session Monitoring which are two critical, complementary capabilities that deliver end-to-end protection across prevention, detection, and recovery stages of a cyberattack.
Behavior Analytics in BMC AMI Security continuously learns the normal behavior of users, applications, and system processes across mainframe environments. By leveraging advanced machine learning and statistical modeling, it identifies & alerts in real-time anomalies that signal potential malicious activity before damage occurs
Why it matters:
- Detects Credential Misuse: Ransomware and insider threats often rely on valid credentials. Behavior Analytics recognizes deviations such as unusual login times, unauthorized dataset access, or privilege escalation and automatically alerts or blocks suspicious activity.
- Prevents Data Exfiltration: Detects data movements inconsistent with business patterns, stopping the extraction or encryption of sensitive datasets before they propagate.
- Reduces Dwell Time: By continuously baselining system activity, it shortens the time between intrusion and detection—often the key difference between a minor incident and a full-blown breach.
- Adaptive Learning: The system evolves as user and workload behaviors change, ensuring ongoing accuracy even in dynamic environments.
Session Monitor provides continuous, real-time surveillance of any user sessions on the mainframe, giving security and operations teams the power to view, record, and analyze every command and transaction as it happens. Its granularity can focus on Privilege Accounts only (if not all sessions needed) with minute by minute snapshots of accounts that begin the moment an account reaches Privileged status.
Why it matters:
- Prevents Lateral Movement: Immediately flags suspicious actions such as privilege escalation, access to critical system libraries, or modification of security policies before attackers can move deeper into the environment.
- Supports Instant Containment: Administrators can terminate sessions or isolate users in real time, preventing the spread of ransomware across LPARs or connected systems.
- Provides Forensic Clarity: In the event of an incident, Session Monitor’s detailed logs and playback capabilities give security teams the exact sequence of events leading to compromise critical for root-cause analysis and compliance reporting
- Accelerates Recovery: Post-incident, the captured session data helps identify affected assets, additional backdoors and privileged accounts that may be left behind while enabling precise and efficient restoration of systems and minimizing downtime.
When used together, Behavior Analytics and Session Monitor form a closed-loop protection system:
- Before an Attack: They detect unusual patterns and attempted intrusions early and report on them to key stakeholders before encryption or data destruction begins.
- During an Attack: They halt malicious sessions, stope executed batches and allow options to preserve forensic data for analysis after an attack has occurred.
- After an Attack: They accelerate recovery through visibility into compromised accounts, affected datasets, and precise event timelines minimizing disruption and ensuring complete restoration.
In short, these capabilities transform mainframe security from reactive monitoring to proactive cyber resilience, giving enterprises the tools not only to defend against ransomware but also to recover faster and stronger if an attack occurs.
BMC AMI Security recognizes that ransomware represents one of the most disruptive threats to enterprise mainframe environments. This includes threats that target not only data but also operational continuity and business trust. As mainframes continue to anchor global financial transactions, supply chains, and government operations, the impact of a ransomware attack extends far beyond IT, it reaches the very core of business resilience. BMC has made it a mission to ensure that prevention and response are not reactive measures, but foundational capabilities built into the heart of mainframe security.
At the center of this mission, BMC AMI Security integrates the principles of the NIST Cybersecurity Framework (CSF) which is Identify, Protect, Detect, Respond, and Recover into every layer of mainframe defense.
- Through continuous asset discovery and behavioral baselining, AMI Security identifies vulnerabilities and risks before they can be exploited.
- Using intelligent access controls and encryption, it protects sensitive system datasets and credentials from unauthorized access or privilege escalation.
- Advanced AI-driven anomaly detection and behavior analytics provide early-warning detection of ransomware indicators, enabling proactive intervention.
- During an active incident, AMI Security automates response actions while halting compromised sessions, terminating batches, and alerting stakeholders to malicious actions. Additionally, AMI will determine what user ID’s were used in an attack, datasets touched and time of attack to determine which immutable backup is safe for recovery. Finally, AMI Security will determine if any backdoors or president threats remain to prevent a repeat attack upon recovery.
- Following an attack, its forensic visibility and detailed session playback allow organizations to recover rapidly, validate the integrity of restored systems, and close gaps to prevent recurrence.
Aligned to the NIST framework, these integrated capabilities provide a structured, continuous loop of protection ensuring organizations maintain operational resilience in the face of evolving ransomware threats. It transforms mainframe security from static protection into an adaptive, intelligent system capable of detecting threats early, containing them instantly, and restoring operations swiftly. This proactive, policy-driven resilience ensures that even in the face of advanced ransomware campaigns, enterprises can continue to operate with confidence by protecting their most critical assets and preserving business continuity.
BMC Mainframe Security offers some unique approaches to harden security and assist in recovery. Modern cyberattacks are no longer simple, one-time breaches, they are persistent, stealthy, and adaptive, often leveraging legitimate user credentials to avoid detection. For organizations relying on mainframe systems to run core business operations, even a brief compromise can have devastating operational and financial consequences.
BMC AMI Security combats this by combining Behavior Analytics and Session Monitoring which are two critical, complementary capabilities that deliver end-to-end protection across prevention, detection, and recovery stages of a cyberattack.
Behavior Analytics in BMC AMI Security continuously learns the normal behavior of users, applications, and system processes across mainframe environments. By leveraging advanced machine learning and statistical modeling, it identifies & alerts in real-time anomalies that signal potential malicious activity before damage occurs
Why it matters:
- Detects Credential Misuse: Ransomware and insider threats often rely on valid credentials. Behavior Analytics recognizes deviations such as unusual login times, unauthorized dataset access, or privilege escalation and automatically alerts or blocks suspicious activity.
- Prevents Data Exfiltration: Detects data movements inconsistent with business patterns, stopping the extraction or encryption of sensitive datasets before they propagate.
- Reduces Dwell Time: By continuously baselining system activity, it shortens the time between intrusion and detection—often the key difference between a minor incident and a full-blown breach.
- Adaptive Learning: The system evolves as user and workload behaviors change, ensuring ongoing accuracy even in dynamic environments.
Session Monitor provides continuous, real-time surveillance of any user sessions on the mainframe, giving security and operations teams the power to view, record, and analyze every command and transaction as it happens. Its granularity can focus on Privilege Accounts only (if not all sessions needed) with minute by minute snapshots of accounts that begin the moment an account reaches Privileged status.
Why it matters:
- Prevents Lateral Movement: Immediately flags suspicious actions such as privilege escalation, access to critical system libraries, or modification of security policies before attackers can move deeper into the environment.
- Supports Instant Containment: Administrators can terminate sessions or isolate users in real time, preventing the spread of ransomware across LPARs or connected systems.
- Provides Forensic Clarity: In the event of an incident, Session Monitor’s detailed logs and playback capabilities give security teams the exact sequence of events leading to compromise critical for root-cause analysis and compliance reporting
- Accelerates Recovery: Post-incident, the captured session data helps identify affected assets, additional backdoors and privileged accounts that may be left behind while enabling precise and efficient restoration of systems and minimizing downtime.
When used together, Behavior Analytics and Session Monitor form a closed-loop protection system:
- Before an Attack: They detect unusual patterns and attempted intrusions early and report on them to key stakeholders before encryption or data destruction begins.
- During an Attack: They halt malicious sessions, stope executed batches and allow options to preserve forensic data for analysis after an attack has occurred.
- After an Attack: They accelerate recovery through visibility into compromised accounts, affected datasets, and precise event timelines minimizing disruption and ensuring complete restoration.
In short, these capabilities transform mainframe security from reactive monitoring to proactive cyber resilience, giving enterprises the tools not only to defend against ransomware but also to recover faster and stronger if an attack occurs.
About BMC
BMC helps organizations run and reinvent their businesses with scalable software solutions that drive the Autonomous Digital Enterprise. For over 40 years, BMC has been a trusted partner to global enterprises, delivering intelligent automation, data management, operations, and security solutions across mainframe and hybrid environments. The BMC AMI (Automated Mainframe Intelligence) portfolio empowers customers to modernize and secure mainframe operations enhancing performance, reducing risk, and ensuring compliance in an increasingly connected and regulated world.